Rigly Newsletter for Epoch 412
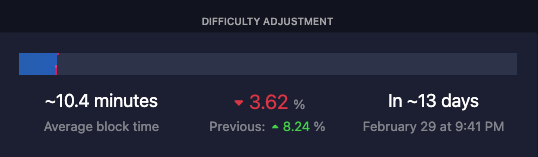
We entered the new difficulty epoch on Thursday, February 15th, block height 830,592.
Bitcoin network difficulty adjusted up +8.24% and is now 81.73 trillion.
Spot Auctions
Buy hashrate at an open market price and start mining right away.
Network Data
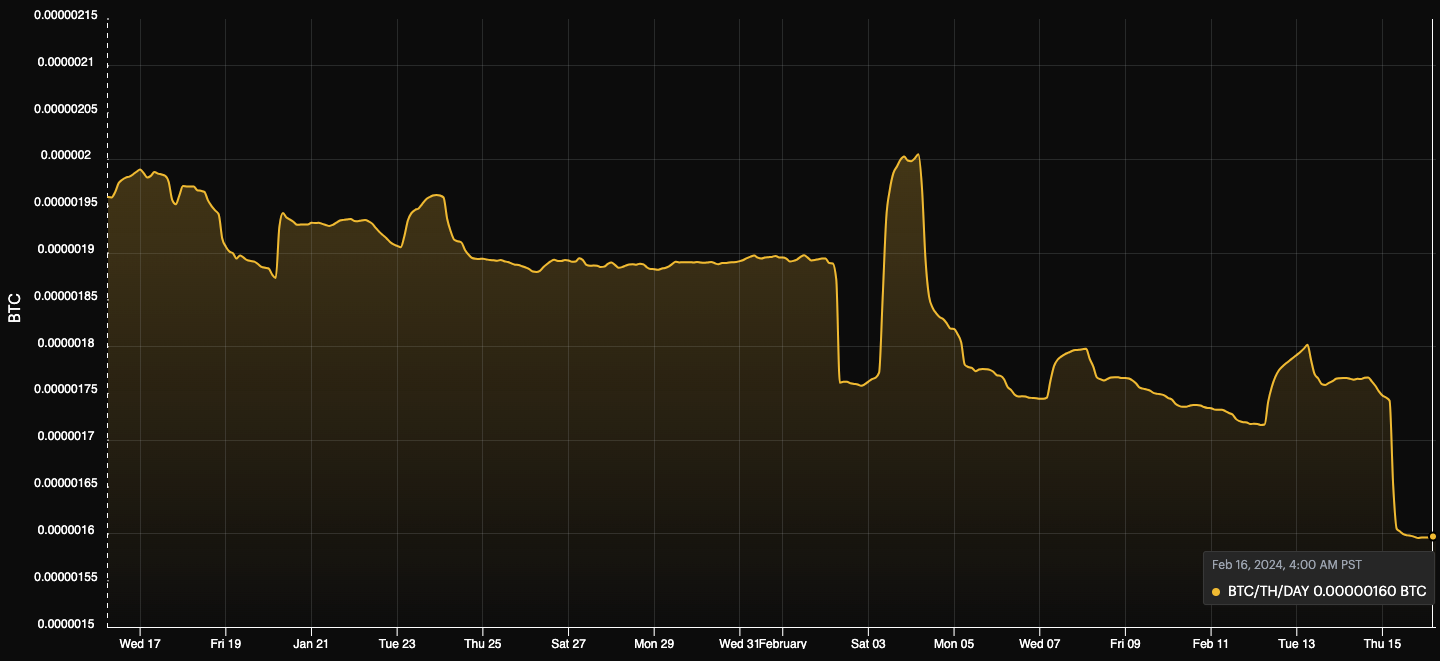
Hashprice
- 160 sats/TH/s/day
Network Hashrate
- Network Hashrate: ~576 EH/s

Difficulty Adjustment
- Epoch 409 / January 5 +1.65%
- Epoch 410 / January 20 -3.90%
- Epoch 411 / February 2 +7.33%
- Epoch 412 / February 15 +8.24%
- Epoch 413 prediction at 80.57T (-1.41%) (Source: btc.com)
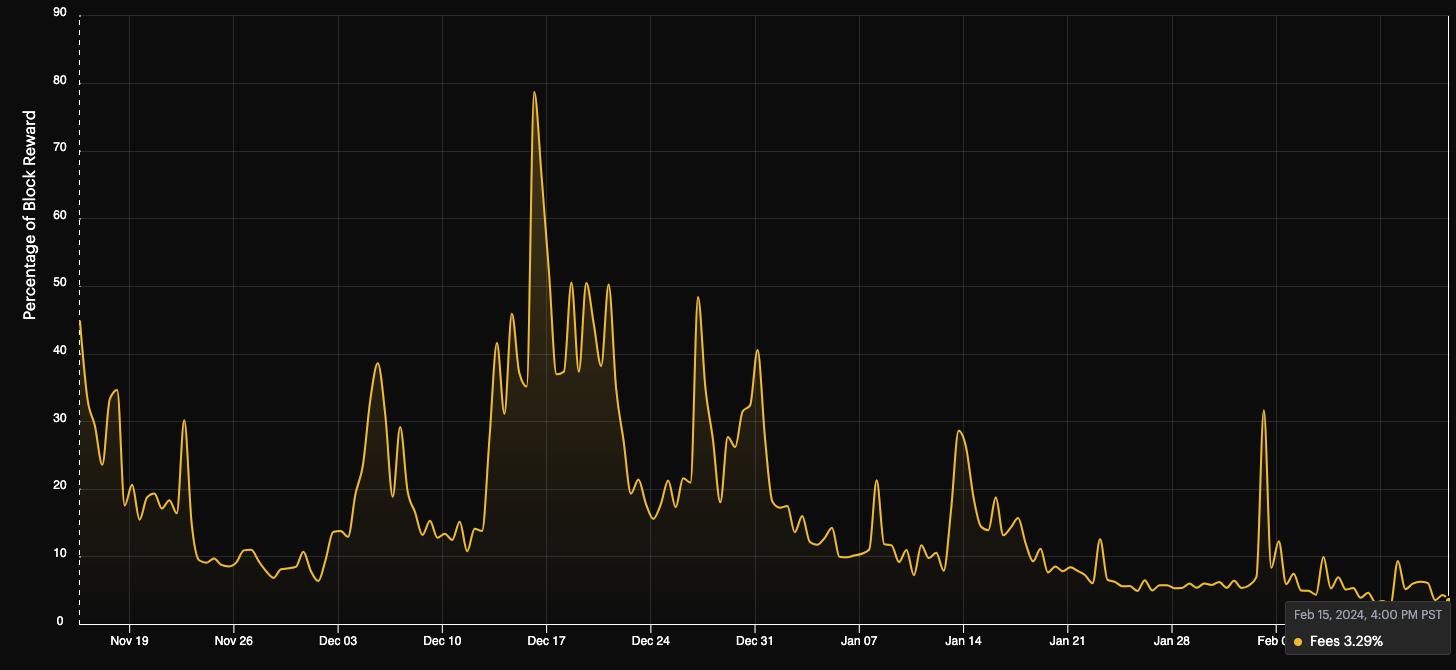
Transaction Fees
Transaction Fees: 3.29% of block reward
🚀
Feb 16th fees were 3.29% of the block reward with a hashprice of 160 sats/TH/s/day.
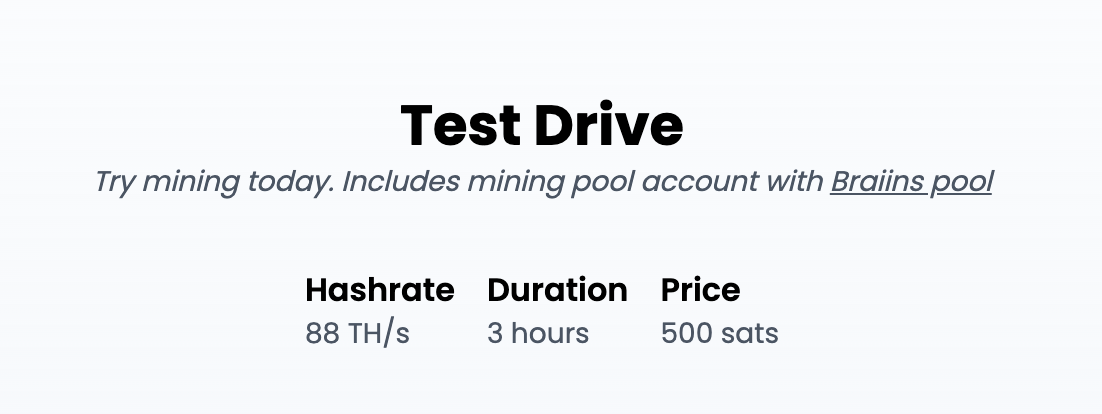
Start Mining for Just 500 sats
Are you still waiting to start your mining journey? Start mining now with our Test Drive for just 500 sats!
Worthwhile Reading
Why Everyone Should Care About Privacy \ stacker news ~tech
Looking for feedback on this article. I am trying to write with the less technical non-bitcoin audience in mind. Why Everyone Should Care About Privacy Privacy is one of those things we hear people talk about and depending upon factors like where you were born, your social status, race, and personal experiences you may have very different views on the subject. One of the most common reactions I hear from people on the topic of privacy is, “I don’t have anything to hide”. I believe this comes from a misunderstanding of what privacy is. Privacy is not secrecy. As Eric Hughes wrote many years ago. A private matter is something one doesn’t want the whole world to know, but a secret matter is something one doesn’t want anybody to know. Privacy is the power to selectively reveal oneself to the world. ~ Eric Hughes - A Cypherpunk’s Manifesto I suspect most people do actually care about privacy but are not aware of what is at risk, who is watching, and what they can do about their own situation. Most people have blinds or curtains on their windows. Most people close the door when we go to the restroom. Most of us don’t share everything we know and think with everyone. These are all privacy choices. Of course these choices involve trust and most of these are not conscience choices we mull over in our minds. We creatures of habit. You are probably thinking, of course. I’m not stupid. Why would anyone just share everything with everyone. OK, now lets talk about your digital life. If you live in the affluent western world and especially the US you probably rarely intentionally think about digital privacy. But ask yourself this. Have you ever started to type something into Google search and paused for a moment to consider it? You probably have. That should tell you something. Your gut is telling you that someone is watching. What is harder to understand is the consequences of being watched. Maybe you’ve never really stopped to think about it but you are making many choices about privacy everyday with your phone and computer. The topic of privacy can be overwhelming. This is one reason why it is important to narrow our focus to a few things when we talk about it. Why should I care? Do you have credit or debt cards? Do have a bank account? Identity theft is often made possible by of mistakes we make with our personal private information. Have you every been asked to provide information online like your birth date or your high school? While this might not seem like a big deal at first, once you realize this info is often used as a component for securing your online accounts it becomes clear why this can be an issue? Many financial services require this info to reset your password for example. Have you ever shared this information online? What could happen is someone gained access to your email account. How many online accounts are connected to that email address? What if someone gained access to your social media accounts. What damage could they do to your reputation? If you don’t follow the information security news you may not be aware that there are data breaches on a daily basis. Hackers gain access to the databases of financial institutions, social media platforms, automotive dealerships, and pretty much any business that keeps its data in a digital format. This means that whatever data you have given these institutions may become publicly available at some point in the future. There are sites that collect data from these breaches and sell it to the highest bidder. The sad truth is that businesses do not take data security seriously enough. They also do not look out for your privacy. It is up to us to do what we can to reduce our own risk, but before we get into what we can do we should talk about what you have to lose. What are the stakes for you? Do you use the same password on every site? If even one of those sites you use leaks your password to hackers those same hackers could access all of your online accounts. You can see how this could quickly become a nightmare if you are caught up in an breach of one of your online accounts. Where do we start I hope you are beginning to see that maybe you should take personal privacy seriously. The best place to start with privacy is to think about what your personal risks are with data. The term used in the privacy and security world for this Threat Modeling. Put simply this the process of creating a model of the possible threats you face with a breach of privacy. Here are a few examples. Journalist High Wealth Individual Politician Political activist/dissident Gun owner Anyone living in an oppressive nation state Employee with access to valuable information Single adult Someone leaving an abusive relationship Parent I could list many more but I hope you get the idea. The average person with modest means living in a relatively free nation has a very different set of risks than someone living in an oppressive nation. But, many of the same tools and approaches can help both decrease their risk. Lets use the journalist example. A journalist might need to protect their privacy to varying degrees but I say a few threat would be. Threats of violence Impersonation Swatting (Falsely reporting that there is a hostage situation to use SWAT teams as a weapon against a target.) Doxing (Making private info like address and phone numbers public) Hacking of phones/computers Financial fraud As you can see journalist must be very careful about their privacy. What about a young woman working at a large corporation. She’s a professional in her late twenties living in an urban area. What are some of her risks? Financial fraud Stalking Hacking of phones/computers Exposing private data publicly Identity theft What about a red blooded American male gun owner. Maybe he has a license to carry a concealed weapon. Maybe he is very bold about his second amendment rights and likes to post photos on social media shooting guns and making bold statements. One day he’s at the gas station and he witnesses an armed robbery taking place and decided to intervene. He stops the perpetrator by shooting and wounding them. What are his risks? For one an attorney for the perpetrator will use his content from social media to build a case against this man. Depending on the jury his social media activity as well as text messages could be used against him in court. So what is your threat model? The Electronic Frontier Foundation has a one page PDF that walks through how do create a threat model. I would recommend going through the process. After you do that take a look at the items I list below. Don’t get overwhelmed. Take it one step at a time based on your threat model. Easy Steps Everyone Should Do Use a password manager like Bitwarden and use a different password for each account you have. Be selective about who you share information with. Push back when you are asked to supply personal information. Use a secure messaging app like Signal instead of SMS, Facebook, Apple messages, or WhatsApp Use a privacy preserving VPN service like Mullvad or iVPN when you are out and about on public WiFi. Steps most people should take Delete social media apps off your phone. You can still use these apps but do it from your computer. Use a privacy respecting email provider like Proton mail instead of Gmail. Advanced Steps Use a privacy respecting phone running GrapheneOS or CalyxOS. Use an email alias service like SimpleLogin. There is much more you can do but these items are a good starting point. [31 comments, 5000 boost]
Terawulf Expands Bitcoin Hashrate to 7.6 EH/s, Repays $22M Debt - TheMinerMag
TeraWulf said it has reduced an additional $22 million of its term loan while increasing proprietary bitcoin hashrate to 7.6 EH/s.

BRICS Enters Bitcoin Mining: China & Ethiopia Sign BTC Miners Deal
BRICS members Ethiopia and China start Bitcoin mining and sign 19 deals with BTC miners who will receive affordable hydropower.

Happy Friday!
Thanks for reading all the way,
Team Rigly